(DRAFT)
Contents:
1.1 Ensure the router is reachable from the internet via DDNS (in case you have a dynamic IP
1.3 Now we come to the really confusing things with Draytek Routers:
1.5 If you use IPsec aggressive mode, the “remote node” must be set.
2.2 Lobotomos Client IpSecuritas
4.2.1 Draytek and certificates
Having some time due to unfortunate circumstances, I occupied myself with VPN.
With Draytek Soho Routers it’s easy to use L2TP over IpSec which is also the most compatible mode (Win, Mac, iOs, Android) to connect securely.
I don’t know if there is some security disadvantage on this but took it as challenge
Before going any further, pls. note
- This is no exact step-by-step manual; if you don’t know about DDNS it probably makes no sence to proceed some things are taken pragmatically
- This is for Soho, not more
- Knowledge about assword security and how to keep them won’t be touched
- No guarantee or resonsability
- Not mentionend here: SSL VPN, PPTP (unsecure), OpenVPN
- IPv6 is not covered
- I am not a native speaker
- My LAN is 10.10.0.0/24, I won’t mention that you have to apply the settings adapted to your LAN
Draytek specialities:
You can here identify the family, your router belongs to: similar firmware numbers indicate similar features/GUIs. E.g. the 2850 belongs to 2920, whereas the 2925 is more professional.
https://www.draytek.com/products/live-demo/
Prelog router side:
Ensure the router is reachable from the internet via DDNS (in case you have a dynamic IP
IPSec and L2TP enabled (note: you don’t have to open the corresponding ports manually within NAT) 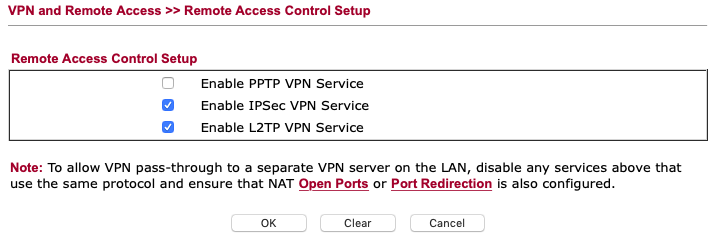
Use these settings in the corresponding menu 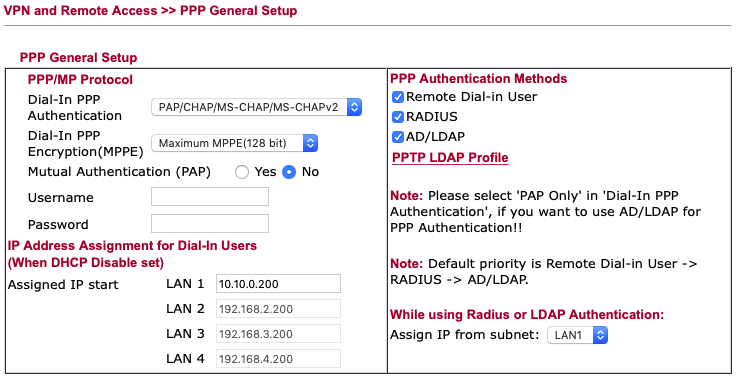
(of course: RADIUS and LDAP could be ticked of: last hint that I don’t go into depth)
Setting a “all purpose” PSK to your remote dial in users
Note you have a PSK setting in the remote dial in user section in the VPN Menu – you can specify a different PSK there if you specify the remote node, see later in this doc.
“Certificate for dial in” won’t appear before we have done with certificate management
The security settings should be exact those in the screenshot (or leave also 3DES). 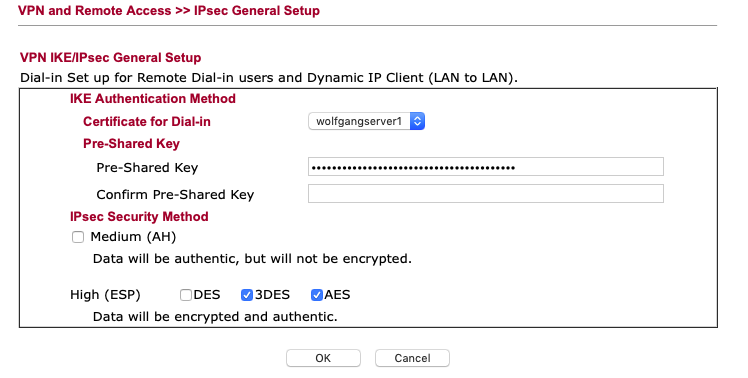
Now we come to the really confusing things with Draytek Routers:
Some fields have ambiguous functions when “L2TP w. IPSEC” and IPSEC are enabled in the same profile so I prefer to make 2 separate profiles which is appropriate with a low cost Soho Router, e.g
if you tick L2TP, you will have to provide a username and a password 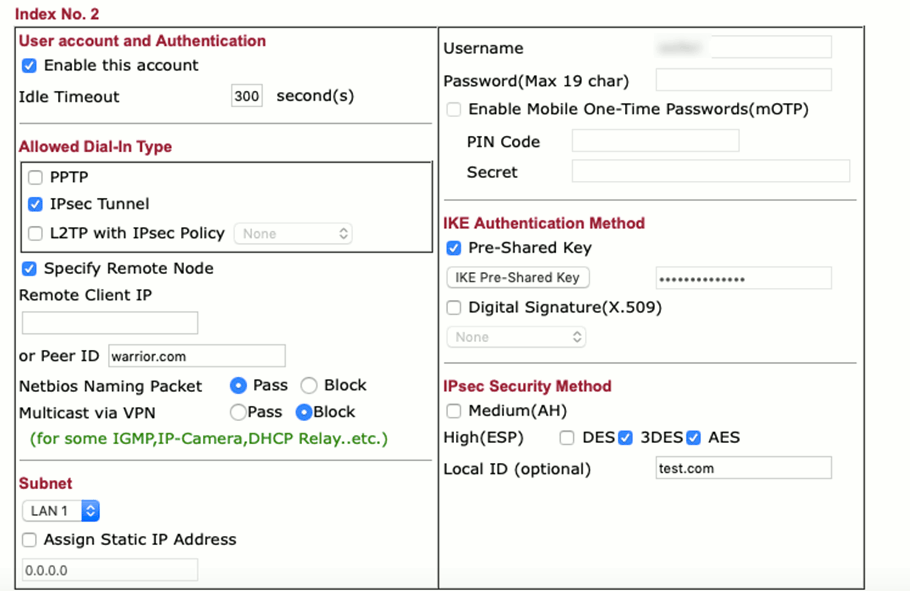
GUI specialities:
If you tick only IPsec, you must insert a username before unticking L2TP… to be able to do so (otherwise you can’t write into this field and you would get an error”); the username then is used as the profile’s name-
If you use IPsec aggressive mode, the “remote node” must be set.
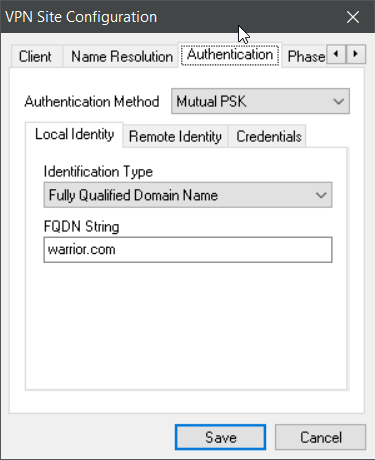
You can use for the Peer ID an IP or a phantasy name (use something that matches a Domain name scheme; if I remember correctly, using “test” caused confusion to a client program). So that peer ID seems to be something encrypted by the Pre Shared Key for identification purposes, it is not a DNS relevant thing here.
Note that only then you can settle the PSK or if you want to use a certificate. According to the documentation, you can set a PSK different from the one in the beginning.
Imaging you have ticked L2TP over Ipsec AND Ipsec (against my proposal): I don’t know what happens if you try to set then a special PSK.
The IPSEC client programs
Shrewsoft: well known, free, google yourself. Win, Linux, Mac.
I didn’t success in installing it on the Mac and didn’t want to spend too much time, so for the Mac I installed
Lobotomos Client IpSecuritas: had a little stomache because it’s free;
difficult to find something (free) for the Mac. The website seems a little cheap so I was unshure whether this could be some Chinese Company or at giveawayoftheday level.
The software is listed at heise. de so I decided that it should be a reputable thing. Decide on your own.
http://lobotomo.com
Note: to install, you should be familiar how to deal with MacOS’ security mechanism warning for programs loaded from the internet (and how to set them trustable).
One special thing: when I first started the program (maybe I did something wrong), I could not make any settings. Now I know it is the same when the program (rarely) get’s stuck:
There is a “Helper Application” component. In such situation: close the main application, then start it again: in the main program menu there you can explicitely close the helper application which closes also the main program, start again (then you should be asked: “the application wants to start a helper application”…. which you should and where your system account password is to be typed in).
Sounds difficult – in other words: you sometimes can’t restart the helper application separately from the main program.
The program has profiles and connections: connection are part of the profiles, for my purpose I use 1 connection for 1 profile.
Duplication profiles is a nice feature to save time.
Note that when duplicating a connection, the corresponding profile gets also the copy as to care for – untick this in the profile, make a new one and apply the clone to the new profile.
Certificate management: I used XCA.
This PDF worked perfectly, use it for training purposes:
http://resources.downloads.pandasecurity.com/sop/pgdi/02sop_pgdiht14.pdf
Nowadays one used 2024 keys, but you are probably not Julian Assange (who doesn’t needs my lines either).
No idea, if SHA1 is too weak here. Guess that draytek supports til SHA256 (not tested)
Examples
The shrewsoft examples are those tested with Win10 whereas the IPSecuritas have been tested with MacOS Mojave.
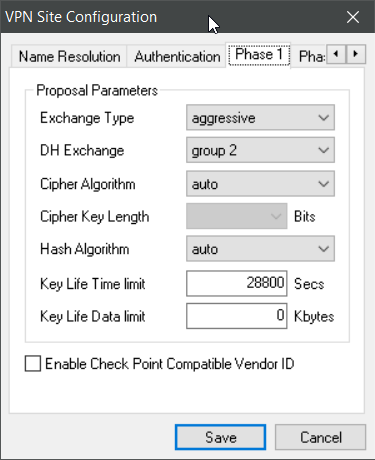
Aggressive mode
Shrewsoft
Your target router`s address to be filled in
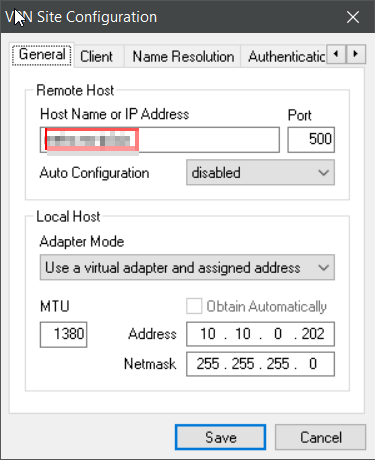
IPSecuritas
Firewall: use your router`s DDNS or IP Address 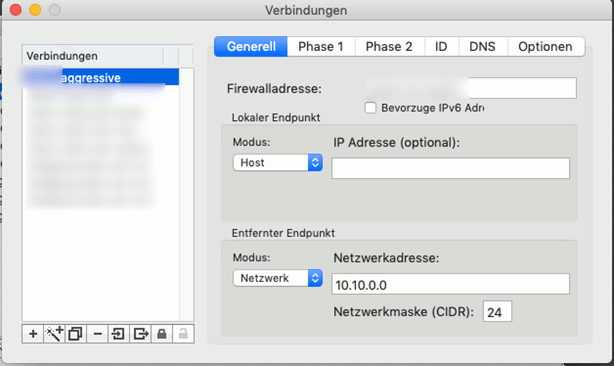
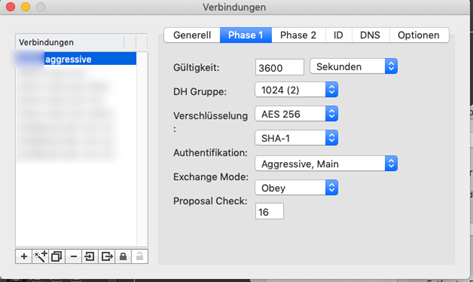
“Aggressive” (solely) would probably be more exact here.
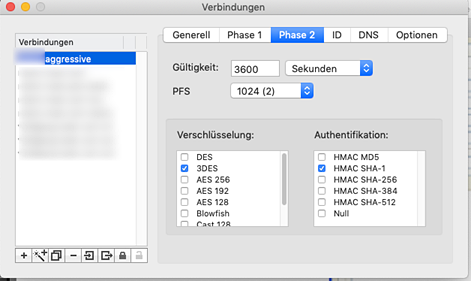
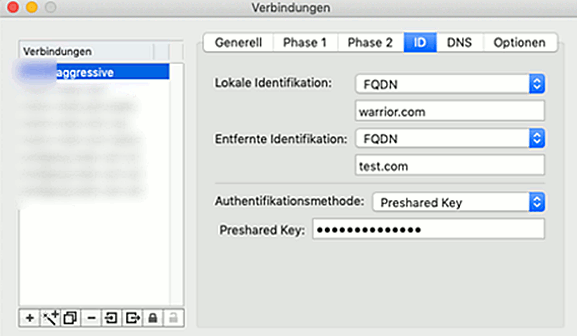
The other tabs can be left at their defaults.
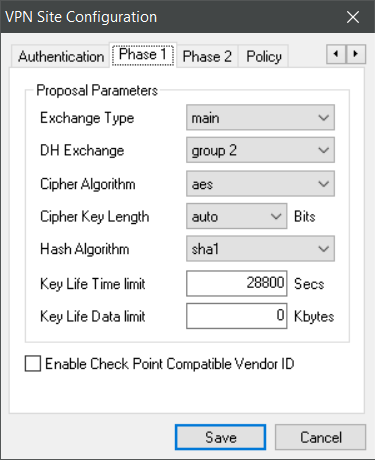
Main mode (not with PSK, you need certificates!)
Draytek and certificates:
First import the CA’s certificate made from the PDF Guide (pandasoft) 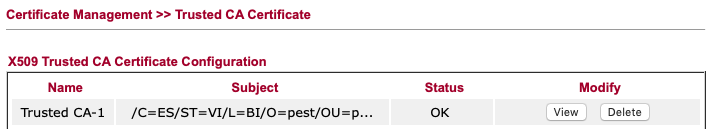
Note: in a few really rare cases you get “invalid file format or password” error, also in the “Locale certificate” section: then reboot the router and try again.
Then we import the server certificate and key (“Generate” wouldn’t simplify the process) 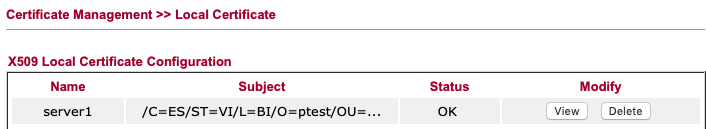
Settle up the peer:
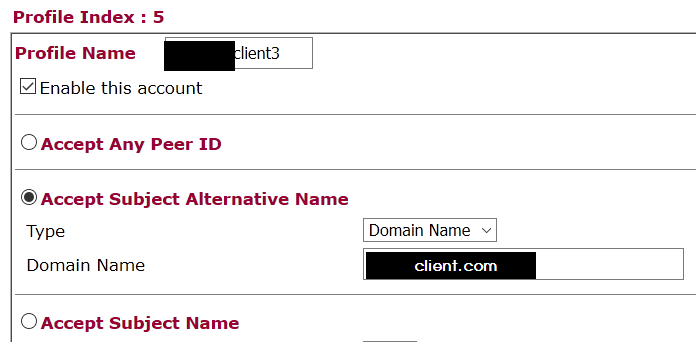
For testing, we generate an “accept all” profile, later you may also define the fields exactly: 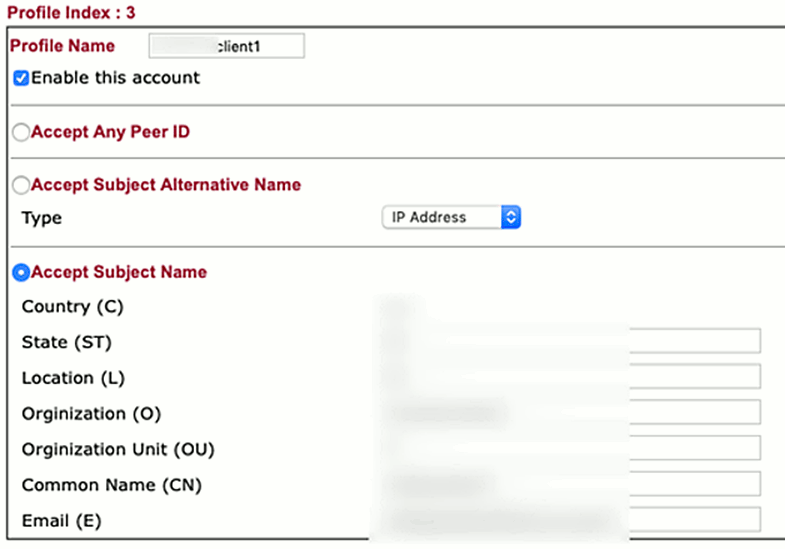
NOTE: with the “Accept Subject alternative name” which is more handy and up-to-date, I had no way to connect with IpSecuritas.
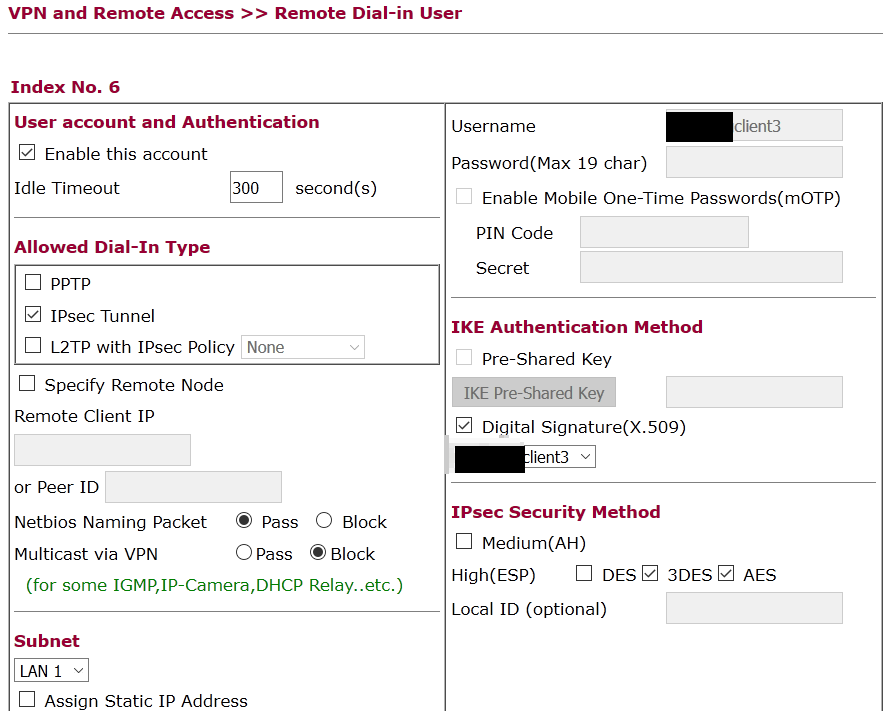
We use this peer identity in the remote dial-in user: 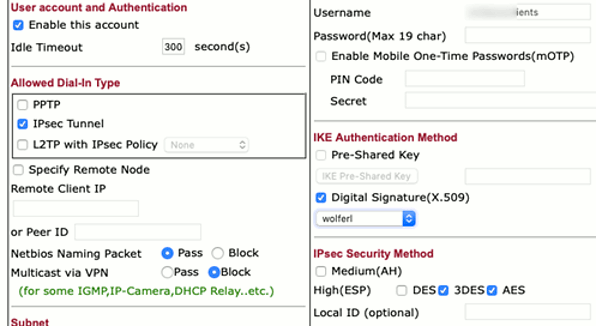
Define the server1 certificate as to be applied alternatively for authentication method 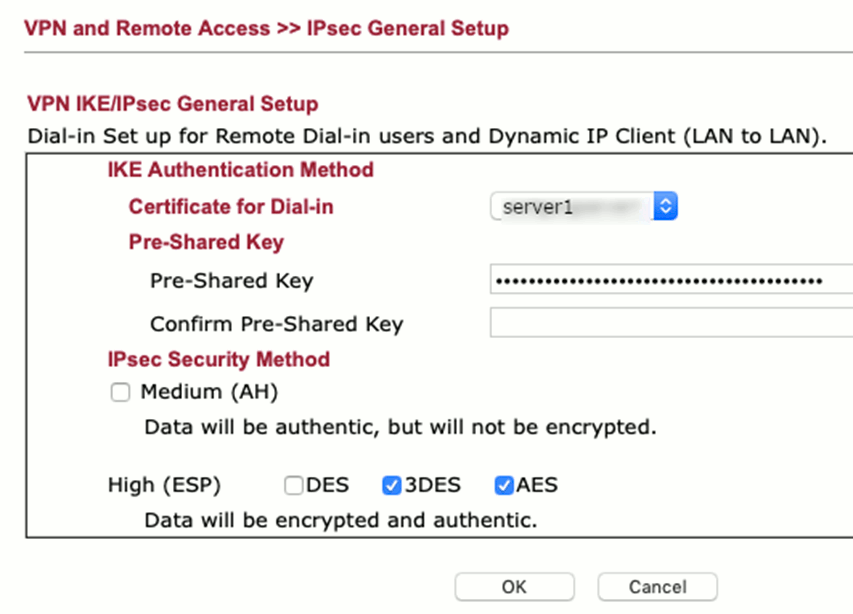
Shrewsoft
Your target router`s address to be filled in
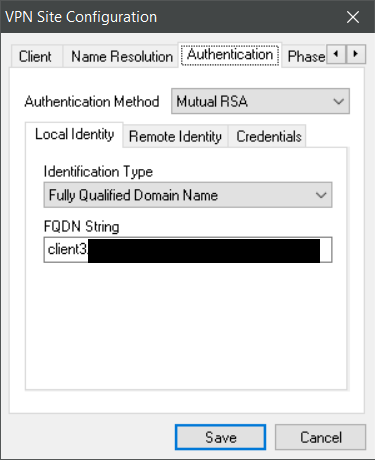
Note: with Shrewsoft, we can use also use the Subject Alternative Name Feature to restrict access to specific users, so here we do this for training purposes.We define a Peer:
make a new remote dial-in-user and tell which peer (client3, right column, middle) to use. (disable the prior defined „any peer id“ profile to ensure the above profile is used.
here of course you import your certificates (see the IPSecuritas section), i.e. the CA’s cert, the clients‘ cert and the client’s private key (if encrypted, shrewsoft will ask for the password when connecting later)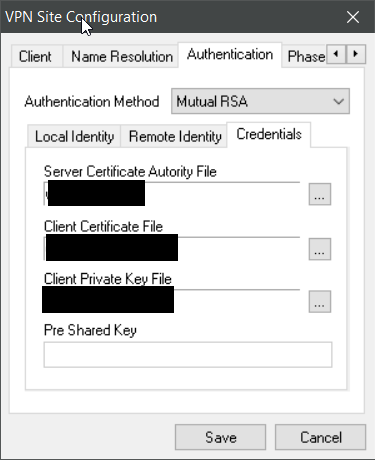
IpSecuritas
First import the certificates made from the PDF Guide (pandasoft) and import them into IPSecuritas (menu “certificates”). You will to import the client’s key with it’s private key and the CA’s public key)
First tab (“general”) is the same as before.
Phase1 here 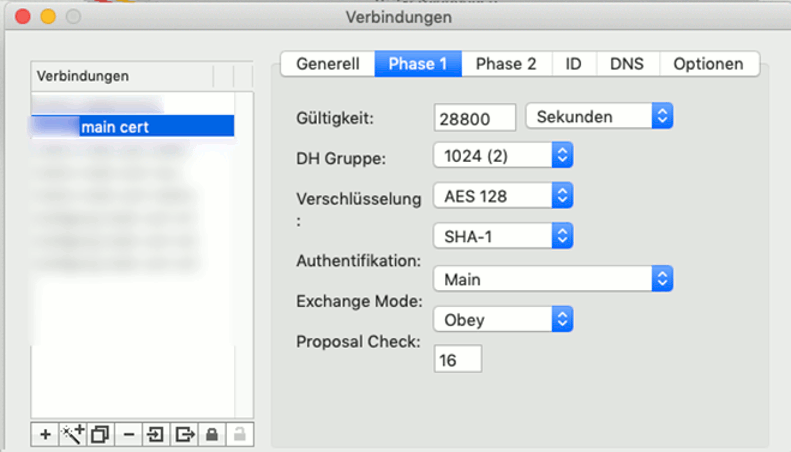
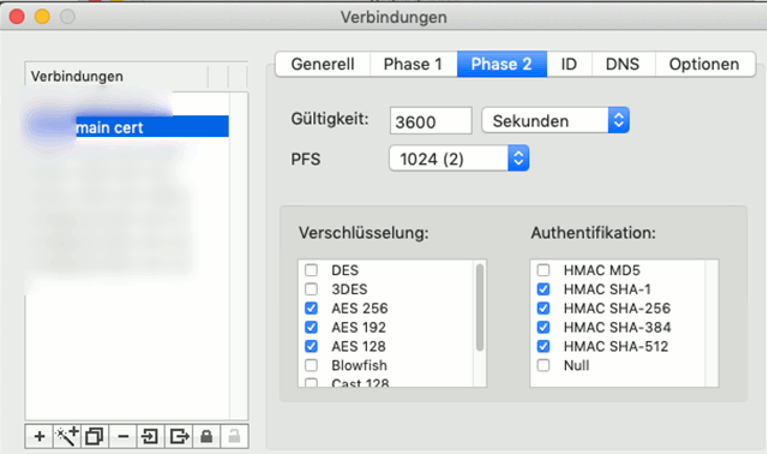
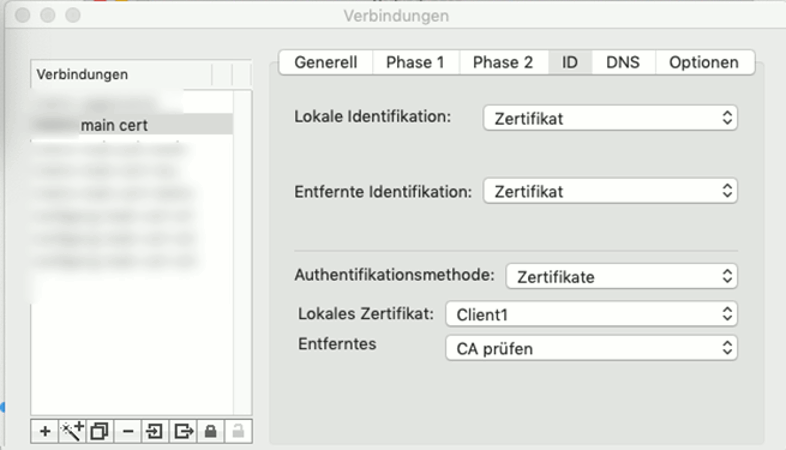
Phase 2: the local certificate has to be the name of the imported client.
DNS-Tab: no changes
Options Tab – no suprises https://findphonebase.ca , I guess.
Consideration on user management – Certificate Revocation List
You will proably think about how to manage disabling users.
Certificates support a revocation list, i.e. an URL where the Server can lookup if a certificate is still valid. Remember that we are here with SoHo, so that the strategy, explicitly en-/disabling users is suffictient.
With Revocation list, I don’t know
- will Draytek look them up?
- what if the CRLS is not reachable? Strict security would mean the server would have to block every certificate the cannot be verified.
If on the other hand the VPN server is generous, a non reachable CRLS would be a security hole.